Online Threats – The 5 Most Vulnerable Job Titles In Your Staff & How to Protect Them

When it comes to online threats, certain job titles are more vulnerable than others. If you run a business, it is essential that you identify these vulnerabilities. It is also crucial that you have preventative measures in place to mitigate the risks of cyber attacks. In this post, we will cover the 5 most vulnerable job titles in an organisation as well as numerous solutions to protect them.
Front-Office Staff/Reception
Front-office staff are vulnerable for a number of reasons, not the least of which is that they are time-poor and often multitasking – attention to information security across all daily interactions is a lower priority than completing multiple job requests. The speed with which they are required to act makes them vulnerable to phishing scams, the installation of malware, browser-based attacks (where they are redirected to fake or compromised websites that attempt to execute code on their browser) and man-in-the-middle attacks (where attackers insert themselves into a two-party transaction).
Position churn in the front office is generally higher than in other areas. This means the information security training load on the organisation is also higher. The result is often that it is delayed or not delivered as effectively, affecting the security posture of the whole organisation.
Your front desk is also a prime location for an in-person attack where a USB key is deployed with a pre-loaded script while, ostensibly, another task is being carried out, say, the printing of a document. Although this would be, by far, the boldest kind of attack it’s worth noting that in security testing the willingness of reception staff to help an attacker solve a seemingly innocuous problem makes it easier to execute this kind of attack.
Accounts Payable
Accounts Payable staff hold the keys to your organisation’s wallet – which places them in a highly vulnerable position as far as fraud is concerned. Accounts Payable staff are also time-poor and have various deadlines to meet throughout the week.
They are highly-compliance driven, accustomed to discussing money, and particularly vulnerable to CEO fraud (where attackers impersonate high-ranking executives to extract fraudulent payments) because of the relationship between senior executives and those that pay the bills. First and Second-generation family businesses are particularly vulnerable to this kind of threat because of the “family” nature of the organisational chart – orders to transfer $100k to a new location are rarely questioned.
IT Department
IT department employees hold the keys to a crucial aspect of your business. – the network. Although you might think IT is the most security-aware and least vulnerable department, we have seen numerous instances where IT decision-makers, even CIO’s, have suffered from professional pride, which can lead to overconfidence and therefore careless accidents. A bit like the ‘I know boats’ guy in this old commercial…).
According to a recent Balabit report, more than one-third of IT professionals see themselves as the biggest internal security risk to their organisations’ networks. This is due to the fact that IT employees often have greater access rights than those in other departments, including access to business-critical data through the IT systems they manage and control. This makes them a key target for cyber attacks.
It also means that disgruntled IT staff know how to gain access to your sensitive information, and could carry out attack themselves if they were so inclined. For example, last year:
- Dutch web host Verelox experienced a major outage of its services after most of its servers were deleted by an ex-employee.
- US-based Allegro Microsystems sued an ex-IT employee for installing malware that deleted critical financial data.
We have first-hand experience of this phenomenon. Computer One staff have taken over networks left with backdoors that were actively under attack from ex-IT staff.
Before your IT staff move on, it is crucial that you insist on system knowledge being written down and backed-up so that you can remove the person if you need to, without removing the IP.
CEO
CEOs may appear in control and untouchable, but they are actually highly vulnerable to online threats.
Often, CEOs use their PC as a personal device, which means they can visit less secure websites or even outright compromised sites, not realising the danger to the organisation in their device being targeted.
They also travel frequently and can often be persuaded to connect to less secure free Wi-Fi that appears trustworthy. This leaves them vulnerable to man-in-the-middle attacks (where they are redirected to non-genuine websites that appear to be genuine).
CEOs are time-poor and extremely busy, and (at least in our experience) this can mean they view information security as someone else’s job to protect them as they go about their business. CEOs can be inclined to underestimate threats, and as a result, may fail to follow correct procedure to mitigate online threats.
Printer
Okay, this isn’t an employee, but it might as well be. Printers can be vulnerable because they are often used with unchanged settings from the manufacturer and placed on less secure networks. Unsecured printers provide a critical staging point for an attack to move laterally in your network.
Also vulnerable are any IoT devices that you use, including air conditioners, fridges, CCTV systems or even… fish tanks. This year, an unnamed casino was hacked via a thermometer in their lobby fish tank. The attackers used the thermometer to get a foothold in the network and gain access to the database of high rollers, which they pulled back across the network, out of the thermostat and into the cloud.
These days any internet-connected asset should be thought of as a productivity aid and a potential weakness.
How to Protect Your Business from These Threats
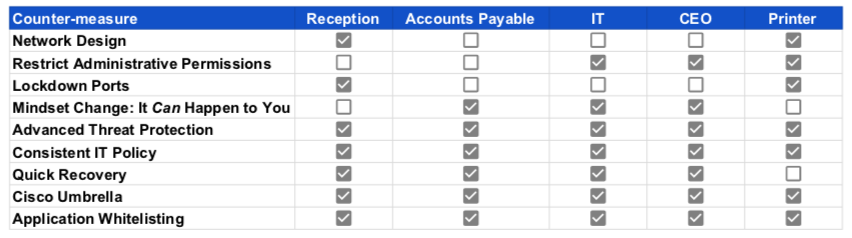
Network Design
Guest users should be on their own network, because by default they’re less trustworthy than company-owned devices which presumably, have been configured by the in-house team with a known operating environment. Printers and other IoT devices too should be isolated from the assets that store and deal in the company’s sensitive information.
Don’t leave easily-exploited tunnels inside your organisation.
Restrict Administrative Permissions
This is part of the ACSC’s Essential 8 – restrict the use of administrative permissions to only the most deserving staff members, and periodically re-examine the permissions to pull them back where you can. All you need is for someone with admin-level permissions to get hijacked and you’re in a lot of trouble, so minimise this attack surface.
Lock Down Ports
This will stop attacks that are spread via USB keys. Particularly effective at preventing information theft by physical object and protecting against an in-person attack. Minimising the attack surface means fewer opportunities for compromise.
Mindset Change
Stop thinking that your business is too small to be targeted. A $100,000 theft is big money to single attackers and organised criminals alike. Thousands of Australian businesses transact dollar values like that every day. You are a target.
Advanced Threat Protection
This is a feature of software available from many vendors that can detect unusual traffic across a network and block or alert you to it for further investigation. Advanced threat protection doesn’t prevent attacks in the first place, but can effectively foil an attack, mitigating the likelihood of a bad actor successfully absconding with your information.
Consistent IT Policy
Set and stick to good IT policy. User onboarding and offboarding should be seamless and able to be executed quickly, so that disgruntled users who are removed from the organisation can’t become malicious insiders.
Quick Recovery
You need to ensure you can recover quickly. New attacks are being crafted daily. These days you can even buy an attack as a service via the Dark Web (read more about this here).
On the assumption that an attack can’t be prevented and will be successful, you should ensure that you have clearly defined the recovery time objective and recovery point objective for your organisation (these terms are defined in this blog post), and test that you can recover to them every 6 months at a minimum.
Cisco Umbrella
Cisco Umbrella software protects businesses by funnelling every external IP request through a database of known good/bad IP addresses and using sophisticated filters to determine the risk of allowing the connection.
Umbrella can prevent you from being part of a wildly-spreading malware campaign. Cisco Umbrella handles more than 80 billion DNS requests per day, so their team’s visibility into underlying patterns of internet traffic is unrivalled.
Application Whitelisting
When it comes to preventing online threats, this is the best solution. If a programme isn’t known and is not permitted to be running, it’s blocked until it receives approval under an application whitelisting solution. With application whitelisting, we have had great success in preventing the execution of malware from running in protected environments. Find out more about application whitelisting.
*
Research suggests that most businesses have unprotected data and insufficient cyber security practices in place, which makes them highly vulnerable to online threats. If you want to protect your business, make sure that you assess the vulnerabilities of every staff member and put systems in place to mitigate the risks of online threats as much as possible.








