We’ve just seen how effective opinion polling in Australia is – the election predictions were completely wrong. So, what better time than now to state with some confidence that Computer One can see the future? We’ll look back in on these in 2022 to see how close to (or how far off) the mark we
It’s a no-brainer to say that asking your clients for feedback is a good idea. But there’s a difference between an occasional survey and automating a constant connection with everyone you deal with. The first scenario results in sporadic improvements. You might catch-on to a budding issue before it costs you a client… but you
What does a good relationship with your Managed IT provider look like? We examined our best client relationships and found these common attributes. Does your current IT relationship look like this or something else entirely? IT is “owned”. No provider is perfect. But the mark of a good provider is being able to admit that
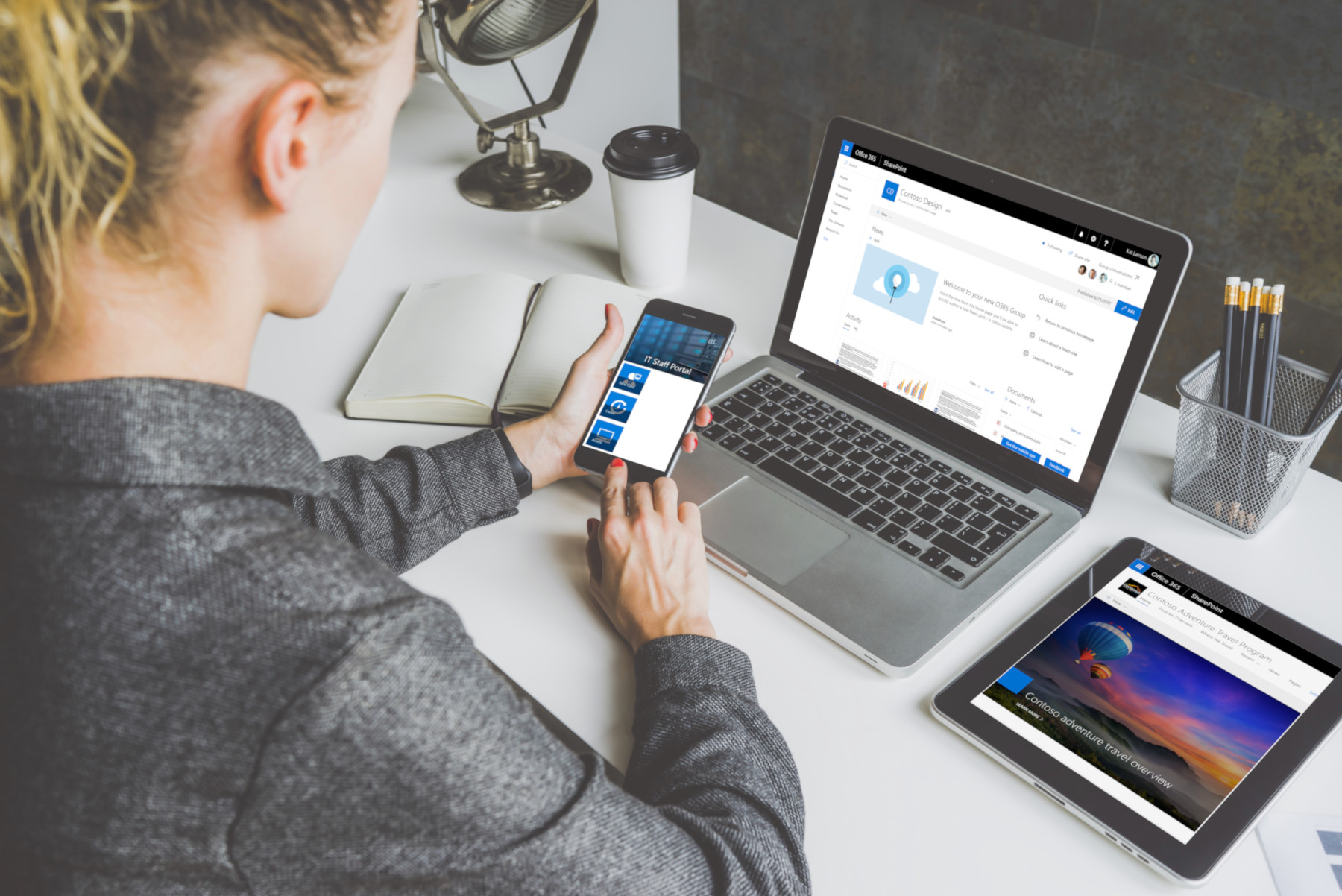
Does your organisation have more than 2 people in it? Do you ever need to share information and collaborate on a document? Are you using Office 365 E1, E3 or E5? Now…are you using SharePoint? If you answered “yes” to the first three questions but “no” to the last, you are missing out on value
No matter if you’re a rusted-on client who would never switch or someone looking for a new Managed IT Service Provider, these three steps will deliver more value without adding extra cost. 1. Get them on-site more often. One of the best ways to get more value from your MSP is to get their staff
Stuck in a one-sided relationship with your IT provider? Spending sleepless nights wondering if they really care? Here are 5 signs which signal that unfortunately, they don’t. Lack of follow up It’s nice when your IT support fixes your problem. But it’s even nicer when they check back in afterwards to see if it has
If you’re still using Windows 7 and loving it, you might not like hearing that the product is nearing the end of its life. Security updates will be cut off in just 5 months: January 2020. That will leave the product untended and vulnerable to new zero-day attacks that are discovered after the support period
Looking for ways to free up some extra cash in your IT budget next financial year? Here are 5 ideas that might contain the answer. Rethink Private Cloud Now you might be thinking, “Whoa, what? How is security of information and guaranteed sovereignty over our data a waste of money?” True, those are genuine business
We’ve been talking about it for years, but this week’s movements at Landmark White show just how seriously the rest of the world takes data breaches these days. Chris Coonan, CEO, has departed with immediate effect citing “…the changing nature of our business and market conditions – combined with major reputational challenges caused by the
Working smarter not harder is our motto at Computer One, and with that in mind, here are two innovative developments that are going to help you kick professional goals this year and next. 5G The latest generation of cellular mobile communications, 5G is slated for launch in the first half of 2019. 5G succeeds the
What Are the Likely Security Threats & Developments for 2019? Cyber threats are always evolving, and 2019 is sure to bring a barrage of new and increasingly sophisticated attack sources and techniques. We expect that 2019 will see an increase in the scope and frequency of cyber attacks, and reckon businesses should prepare for multi-pronged
Back in mid-2017 Microsoft released a product called simply: “Microsoft 365: Enterprise”. Its primary target was the high-end commercial market and that’s where the product has been making inroads ever since. But did you know there’s also a version for Small to Medium businesses up to 300 seats? It’s attractively-priced and it’s packed full of
As far as cyber security was concerned, 2018 didn’t get off to a great start. Just days after people celebrated the new year, researchers announced a vulnerability that had been found in basically every CPU processor that had been made in the last 20 years. The most common security threat types in 2018 were malware,
According to Verizon’s 2018 Data Breach Investigations Report, 92.4% of malware is delivered by email. Up until now, phishing emails have been easy to spot because they come from suspicious email addresses and include poor grammar and formatting – when you think of a phishing scam, you probably picture one of those poorly worded emails
An attack vector is the means by which a hacker gains access to your computer or network server, in order to engineer a malicious outcome. Through various attack methods, hackers can exploit system vulnerabilities of all sorts (including the human element, i.e. your staff). In this post, we will explore 5 common attack vectors and