Email Phishing Scams Are More Sophisticated & Prevalent Than Ever

According to Verizon’s 2018 Data Breach Investigations Report, 92.4% of malware is delivered by email. Up until now, phishing emails have been easy to spot because they come from suspicious email addresses and include poor grammar and formatting – when you think of a phishing scam, you probably picture one of those poorly worded emails that ask you for money (perhaps from the perspective of a Nigerian prince or an imprisoned foreign diplomat).
You might think that your business is safe from phishing scams because none of your employees would fall for such an obvious trick. The problem is, these days, email phishing scams are more sophisticated – and prevalent – than ever.
What Is a Phishing Scam?
Phishing scams are emails that try to persuade the opener to download malicious attachments, click on dodgy links, make payments or provide personal details or other sensitive data. Phishing emails often contain a high sense of urgency or privacy, discuss confidential subjects, offer some sort of reward and contain links or attachments. You can read more about the different types of phishing in this blog post – Phishing, Spear-Phishing and Whaling – What’s the Difference?
As far as businesses are concerned, phishing attacks are often used to deliver ransomware onto an organisation’s network – the software then encrypts files or locks computer screens until a ransom is paid. Because the ransom amount is usually quite small, many businesses hastily pay the money, even though there is no guarantee that their system will be unlocked.
According to Symantec’s 2018 Internet Security Threat Report, the most common disguises when it comes to distributing malware are:
- Bill/invoice (15.9%)
- Email delivery failure (15.3%)
- Legal/law enforcement (13.2%)
- Scanned document (11.5%)
- Package delivery (3.9%)
Here’s An Example of an Unsophisticated Phishing Scam Email

You have probably received emails like this. Although unwary citizens may fall for these phishing emails, cybercriminals have realised that they need to up their game if they are going to successfully deliver malware or acquire data from organisations.
Today, your business is more likely to receive emails with forms or attachments that look like this:
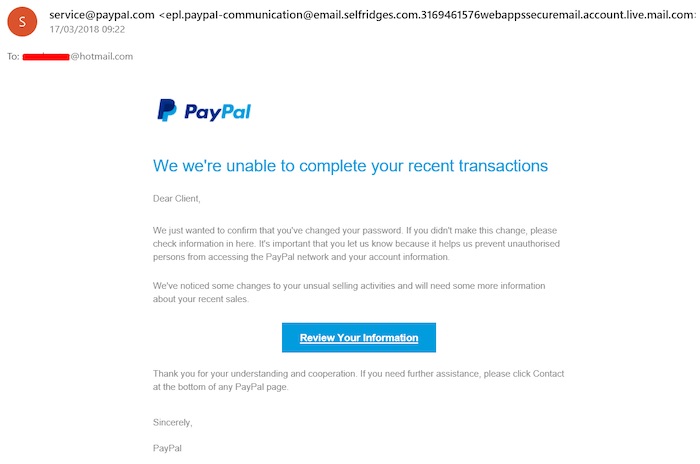
Through the use of logos, layouts, signatures and email addresses that are very close to the originals, it’s easy for fraudsters to create emails that appear legitimate. The phishing email above looks very close to an actual PayPal email, so rushed employees could easily make the mistake of clicking the link.
To make sure that your employees don’t fall for scams like this, make sure that they always double check the sender’s email address, and let them know that emails from reputable senders often use ‘Dear [client’s full name] as opposed to just ‘Dear Client’. Also, emails from legitimate businesses rarely request the following information:
- Full bank or credit card number
- Debit card PIN numbers
- Driver’s license number
- Email addresses
- Street address
- Full name
- Passwords
- Answers to security questions
Your Staff Are Vulnerable
Whether you admit it or not, your staff are becoming increasingly vulnerable to sophisticated email phishing scams. You can train your staff to be on the lookout for suspicious emails and indeed, we deliver such training, but as it gets harder and harder to distinguish illegitimate phishing emails from real communications, you also need new lines of defence.
Phishing Protection
Email is the most important business communication tool, and it’s also your organisation’s top security vulnerability. Here are some practical actions you can take to prevent and reduce the effects of phishing scams:
Barracuda Essentials Email Security
Barracuda Essentials is a comprehensive service that protects users against spam, malware, phishing emails and more. Barracuda Essentials includes a range of microservices, such as advanced threat protection over email, tamper-proof archiving and data protection – it can protect your business from the most advanced email attacks.
Application Whitelisting
Application Whitelisting is designed to protect your endpoints from malicious code, by allowing only authorised applications (including installers, programs, scripts, et cetera) to run on your system. All untrusted executables and scripts are blocked by default, even if your system is unpatched. The control panel is easy to use to resolve false positives so that your organisation can continue to work uninterrupted by delays.
Application Whitelisting will protect your organisation from phishing and spear-phishing attacks, and will also prevent:
- Ransomware
- Stuxnet type attacks against Industrial Control Systems
- Watering Hole type attacks where a compromised website tries to execute commands via your Internet browser
- Droppers from compromised Websites
- Keyloggers and similar trojans that might be installed through other compromised software or via a direct attack
- Internet Worm type attacks like Wannacry and Not Petya from 2017.
As email phishing scams grow in sophistication, now is the best time to start implementing your defence strategies. If you have any questions about the information in this post or how your organisation can protect itself against email threats, don’t hesitate to call us on 1300 667 871 or get in touch.








